|
|
|
|
 |
 | |  |
| Since she does not want me back, Im going to install a key logger on her computer. | |
 | |  |
|

|
|
|
Key loggers are serious threat to our personal information.
|
|
|
|
 | |  |
| My credit card information was obtain and used for unauthorized online purchases. My email account, websites that I visit, instant messages and all my email messages are easily detected. | |
 | |  |
|
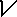
 |
|
|